Focus and Scope
The International Journal of Cyber Forensics and Advanced Threat Investigations is supporting a forum for both theoretical and applied aspects of cybersecurity and is elaborated in two versions: a theoretical version, including original articles whose contents have never been published before, and a version including articles of applicative quality, relevant for their technological contents and aiming at practical results. An important part of the mission of the Journal is to promote cybersecurity, digital forensics, incident response, and threat investigations.
The journal aims to bring together researchers and practitioners working on related fields of cybersecurity, digital forensics, incident response, and threat investigations, to report new developments and latest proven methodologies, and to publish scholarly articles presenting current research issues and advances. The Journal also aims to provide insights for the discussion of the major research challenges and achievements regarding the theory, research, and practice in these rapidly changing topics.
We encourage contributions describing innovative work in the realm of the measures that governments or organizations should follow to protect the online information & critical infrastructure, the impacts of cyber-crime & cyber-attacks in organizations and/or individuals, malware/ransomware, analysis & reversing, hardware/software security testing, zero-day attacks & exploits, large-scale digital investigations, unconventional penetration testing tactics, techniques & tools, social engineering & human hacking, anti-forensics & anti-anti-forensics, identity theft & protection, women in cybersecurity & challenges faced by women in cyber forensics, relevant case studies in cybersecurity, digital forensics, incident response, & threat investigations, and proficient strategies for tackling the various types of cyber-attacks and cyber-crimes.
The following is a non-exhaustive list of topics that fall within the scope of the journal. Other non-listed topics that fall under the general cybersecurity umbrella are also of interest to the Journal. Topics covered include:
• Data leakage, Data protection, and Database investigations
• Executable Content and Content Filtering
• investigations of Virtual and Cloud Environments
• Investigation of Insider Attacks
• Malware investigations and Anti-Malware techniques
• New threats and Non-Traditional approaches
• Reverse engineering
• Threat Hunting and Intelligence
• Incident Management and Analysis
• Machine learning applications in cybersecurity and threat intelligence
• Focus on women's perspectives in cybersecurity, digital forensics, incident response, and threat investigations and challenges faced by women in these fields,
• Adversarial machine learning
• Advances in critical infrastructure security
• Privacy-enhancing techniques
• Evidentiary Aspects of Digital investigations
• Internet of Things, Smart Grid, Smart Car and Drone Forensics
• Ongoing integration of Artificial Intelligence/Deep Learning/Decision Support methodologies in Law Enforcement & Police Investigation
• File System and Memory Analysis
• Multimedia investigations
• Information Hiding, Steganography, and hidden data Analysis
• Large-Scale Investigations
• Vulnerability Management, Ethical Hacking, zero-day attacks, attack pattern recognition
• Network investigations and Traffic Analysis
• Hardware Vulnerabilities and Device investigations
• Computational Immunology, Authentication Authorizations
• Security in Mobile Platforms, Mobile Agents/Artificial Intelligence
• Security Policies/Procedures, Strategic Approaches, Requirements Engineering
• Identity Theft, Management Systems, Access Management Systems
• Open-source intelligence, criminal data mining/network analysis/intelligence, and digital forensic intelligence.
• Phishing/pharming/spearphishing, cyberwar, cyber-crime detection/analysis
• Digital cities, GSM-solicited crime
• Computer/mobile device/network/software forensics, anti-forensics
• Digital forensics tools/techniques/standardisation, testing/approvals for forensic tools
• Crime scene/search and seizure processes, criminal investigation of mobile devices
• Investigative techniques, judicial processes, legal/ethical issues, cyber-crime legislations
• Digital and physical surveillance, digital image manipulation
• Cryptography for cybersecurity, algorithms/protocols,
• Cybersecurity training and education,
• Open source cybersecurity tools, solutions, and applications.
• Current and future trends in Security, privacy, and trust in 5G/6G networks
• Blockchain technology and Cryptocurrency based trust systems.
• AI-driven Software-Defined Security, privacy, and trust
• Smart security of future connective systems
• Security analysis of existing cryptocurrencies.
• Game theory in aid of cybersecurity
Section Policies
Research Articles
Regular articles are full-length original empirical investigations and research, consisting of an introduction, materials and methods, results and discussion, conclusions. Original work must provide references and an explanation of research findings that contain new and significant findings. Along with the abstract, all research article submissions should include ‘Notes for Practice’ that highlight the significance of the work for practice. These notes should be comprised of bullet points outlining:
- A brief accessible overview of the established knowledge on the topic
- A summary of the contribution of the article
- Key implications of the article’s findings for practice, policy, and implementation of research
Each research article should lie within one or more of the basic cybersecurity methodologies either red teaming methodology, yellow teaming methodology, or blue teaming methodology. This will aid to reduce the time required to nominate prospective reviewers for the article.
Note: The research article should be at least 6 full pages and at most 30 pages (excluding the abstract, references, tables, and/or figures), a minimum of 7 references with 20% of the references should be from recent articles. Use a reference manager, such as Mendeley, Endnote, or Zotero to improve the quality of the article. An abstract of 100–200 words. Finally, It is advisable for the authors to consult the previous articles with similar topics, published in the journal.
Practical Articles
Practical article examines a subject of analysis in cybersecurity, digital forensics, incident response, and threat investigations in order to extrapolate key themes and results that help predict future trends, illuminate previously hidden issues that can be applied to practice, and/or provide a means for understanding an important research problem with greater clarity. A practical article usually examines a single subject of analysis, but practical articles can also be designed as a comparative investigation that shows relationships between two or among more than two subjects. The methods used to study a practical case can rest within a quantitative, qualitative, or mixed-method investigative paradigm. Along with the abstract, all practical article submissions should include ‘Notes for Research’ that highlight the significance of the work for research. These notes should be comprised of bullet points outlining:
- What prior research findings do this practical article draw on
- What new contributions do the practical article make
- What significance does this have for researchers (contextualize existing findings, suggest new areas needing research, etc.)
Each practical article should lie within one or more of the basic cybersecurity methodologies either red teaming methodology, yellow teaming methodology, or blue teaming methodology. This will aid to reduce the time required to nominate prospective reviewers for the article.
Note: The practical article is about 6-30 pages, include appropriate figures and/or tables, and an abstract of 100–200 words.
Review Articles
Review article is a critical evaluation of materials about current research that has already been published by organizing, integrating, and evaluating previously published materials. It summarizes the status of knowledge and outlines future directions of research within the journal scope. It aims to provide systemic overviews, evaluations, and interpretations of research in a given field. The manuscript title must start with "Review Article:".
Each review article should lie within one or more of the basic cybersecurity methodologies either red teaming methodology, yellow teaming methodology, or blue teaming methodology. This will aid to reduce the time required to nominate prospective reviewers for the article.
Note: The review article is about 6-30 pages, include appropriate figures and/or tables, and an abstract of 100–200 words.
Hot Spot Notes
Hot Spot Notes are short industry case reports about emerging hot topics. Hot Spot Notes accurately document factual data as well as the settings, actions, behaviors, and consequences that are observed. They may also contain the thoughts, ideas, questions, and concerns that arise as the observation is conducted. Hot Spot Notes provide perspectives on a single phenomenon that, when accumulated over time, suggests new avenues of research.
To propose a Hot Spot Notes, please email the editors at cfati@conceptechint.net with:
- A short summary of the proposed Hot Spot Notes
- The proposed reviewers' biographies
- A short rationale for why these Notes are worthy of publication / will be of interest to the CFATI audience
All prospective reviewers must adhere to our ethics and conflict of interest policy: they are expected to not have close personal or collegial relations to the authors of materials they propose to review, nor any vested interest in the promotion or sale of certain products/services. Unsolicited reviews are accepted. Please do not send the Hot Spot Notes without first proposing it and having it approved by the editors. Commissioned reviews will be given careful editorial attention and a dialogue with the reviewer may occur before a final version is accepted.
Case Studies
Investigative case studies and reports describe how practitioners are dealing with emerging challenges in related fields of cybersecurity, cyber defence, digital forensics, incident response, cybercrime, and threat investigations along with highlighting areas that require further research, development, or legislation. Also, case studies establish a meaningful forum between practitioners and researchers with useful solutions in various fields of cybersecurity, cyber defence, digital forensics, incident response, cybercrime, and threat investigations.
The format for a case study is simple and short: abstract, case Introduction, any technical or legal challenges, the digital evidence involved, processes and/or tools used, outcomes, recommendations, and conclusions. The case study can also include all kinds of practical applications, which cover principles, projects, missions, techniques, tools, methods, processes, etc.
Legal Analysis Reports
Legal analysis reports are accurate comments by legal experts on recent cases related to legal measures that governments or organizations should follow to protect the online information and critical infrastructure, the impacts of cyber-crime and cyber-attacks in governments, organizations and/or individuals, cybersecurity applications, cybercrimes and threat investigations, guidelines on seizing digital evidence, counter-terrorism and surveillance-related legal developments, recent legal developments in social media and multimedia analysis strategies, data protection and privacy issues, and legislative restrictions.
To submit a legal analysis report, please submit the following:
- A short summary of the proposed legal analysis report
- The proposed reviewers' biographies
- A short rationale for why this report is worthy of publication / will be of interest to the CFATI audience
All prospective reviewers must adhere to our ethics and conflict of interest policy: they are expected to not have close personal or collegial relations to the authors of materials they propose to review, nor any vested interest in the promotion or sale of certain products/services. Commissioned reviews will be given careful editorial attention and a dialogue with the reviewer may occur before a final version is accepted.
Report on Tool and Tool Application
Reports on Tools and Tool Applications describe and evaluate software tools and tool applications in the journal's areas of interest, e.g., cybersecurity tools, tools for digital forensics, incident response, and threat investigations, and software architectures of such tools. A submission to this section should describe and justify the tool design including all relevant design objectives and requirements, design alternatives and decisions, and its software architecture. The tool description should focus on the specific features of the tool and relate the tool to other tools and prior related work. It is strongly encouraged that the described tools are freely available (i.e. Libre/Free/Open Source Software at best) . If this is not possible, they have to be made available to the reviewers for the reviewing process (please email the editors at cfati@conceptechint.net for an arrangement). Submissions to this section are double-blind peer-reviewed by at least two reviewers (with review criteria adapted to the specifics of this section), and must adhere to scholarly standards in terms of originality, level of abstraction, and justification.
International Workshops/Conferences of CFATI
CFATI Journal sponsors conferences, seminars, or workshops in related areas on a case by case basis. CFATI Journal may invite conference organizers or chairs to serve as guest editors for special or themed issues publishing selected papers from the conference proceedings. Interested parties are encouraged to contact the editors at cfati@conceptechint.net with their proposals and they are subject to approval by the journal editor-in-chief.
The names of the guest editor(s) and editorial board members for a special or themed issue will be published in that issue. If it is a special issue of a conference proceedings, the details of the conference and the proceedings papers will be cited.
This section is a special issue of selected and revised articles from the International Workshops/Conferences of CFATI after peer-reviewed by CFATI's Editorial Board and Reviewers. Only registered participants can submit their papers.
Special Issue Articles
In order to better serve our academic community and concentrate on highly interest, special issues of any subjects in cybersecurity, digital forensics, incident response, and threat investigations are welcome at any time. A special issue should be organized by accomplished experts in a given area and it should attract articles of the highest quality.
Proposals of special issue should include the following information:
- A suggested title for the Special Issue
- Number of expected article to be accepted
- The timeline of the special issue until it published
- Proposed Aims and Scope with an outline of the Special Issue's intended focus and a list of the topics to be covered
- Names of Guest Editors who are willing to manage the Special Issue with their emails, affiliations, and an one-paragraph biography of each of the Guest Editors
All proposals should be submitted to the editors at cfati@conceptechint.net and they are subject to approval by the journal editor in chief.
Book Reviews
Book Reviews proposals are welcomed by the Journal of Cyber Forensics and Advanced Threat Investigations. Reviews inform readers about recent publications relevant to cybersecurity, digital forensics, incident response, and threat investigations, and the use of cybersecurity tools in education. Reviews may be of single books or can be review essays that discuss and compare two or more books addressing related topics. Reviewers must have sufficient up-to-date expertise in the topic(s) of the book they propose to review and familiarity with the literature of the Cyber Forensics and Advanced Threat Investigations field overall. The book reviews should be no more than 8,000 words in length and provide a concise introduction to the book's primary topics, themes, and messages followed by a critical analysis of its strengths, weaknesses, and relevance to the field.
To propose a book review, please email the editors at cfati@conceptechint.net with:
- The citation and a brief description of the book proposed for review
- The proposed reviewer's CV
- A short rationale for why the book is worthy of review / will be of interest to the CFATI audience
All prospective reviewers must adhere to our ethics and conflict of interest policy: they are expected to not have close personal or collegial relations to the authors of materials they propose to review, nor any vested interest in the promotion or sale of the book. Unsolicited reviews are not accepted. Please do not send a review without first proposing it and having it approved by the editors. Commissioned reviews will be given careful editorial attention and a dialogue with the reviewer may occur before a final version is accepted.
Letter to the Editor
Letters may discuss previously published material or commentaries in the International Journal of Cyber Forensics and Advanced Threat Investigations (CFATI) or any issue of interest to the International Journal of Cyber Forensics and Advanced Threat Investigations (CFATI). Letters commenting on the published material are shared with the original authors to give them an opportunity to respond. Interested parties are encouraged to contact the editors at cfati@conceptechint.net with their letters and they are subject to approval by the journal editor-in-chief.
Peer Review Process
This journal operates a conventional double-blind reviewing policy, which means that both the reviewer and author identities are concealed from the reviewers, and vice versa, throughout the review process. Authors should present their articles honestly without fabrication, falsification, plagiarism, or inappropriate data manipulation. Submitted articles are evaluated by anonymous referees for contribution, originality, relevance, and presentation.
Upon submission of any manuscript for consideration for publication in a journal published by Concept Tech Publishing, the scientific editor first scans it for plagiarism to verify its originality, then performs a search of the Web of Science, Scopus, Google and/or IEEE databases to determine the topical relevance and timeliness of the manuscript’s content as well as to make an initial assessment of potential academic misconduct related to the general features of the study and/or topical content. The results of this initial review are either approval to enter into the peer review process (double-blind peer review) or rejection. The first step in the peer review process involves the delivery of the manuscript to 1 to 3 external reviewers with expertise in the paper’s topic and/or field, at least one reviewer who will either be a member of the Editorial Board or others of similar standing in the field. The reviewers are allotted a period of 30 to 60 days in which to thoughtfully assess the manuscript and return comments to the editorial office, at which time the editorial director conducts a decision-making meeting to assess the reviewers’ comments. Manuscripts that have received positive comments and meet the general publication requirements of Concept Tech Publishing and any specific requirements of the particular journal are forwarded directly to the editor-in-chief, who provides signatory approval recommending that the manuscript is “To Be Accepted”. If the manuscript fails to meet the high-quality standard assessed by the peer reviewers or does not meet the Concept Tech Publishing and/or journal-specific criteria, it is rejected. All manuscripts recommended for acceptance must pass a final review by the editor-in-chief before they are officially accepted for publication and entered into the production phase. The scientific editors’ decisions are final and no correspondence can be entered into concerning manuscripts considered unsuitable for publication in this journal. All correspondence, including notification of the Editors’ decision and requests for revisions, will be sent by email.
CFATI journal has four kinds of decisions:
- Publish as is, Accepted, as it is
- Publish with minor corrections or additions, Accepted by Minor Revisions, and let authors revised with a stipulated time.
- Major changes and a second review are required, Major Revisions are required. The authors revise with a stipulated time, then resubmit for a second review.
- Reject, Generally, on grounds of outside of scope and aim, major technical description problems, lack of clarity of presentation.
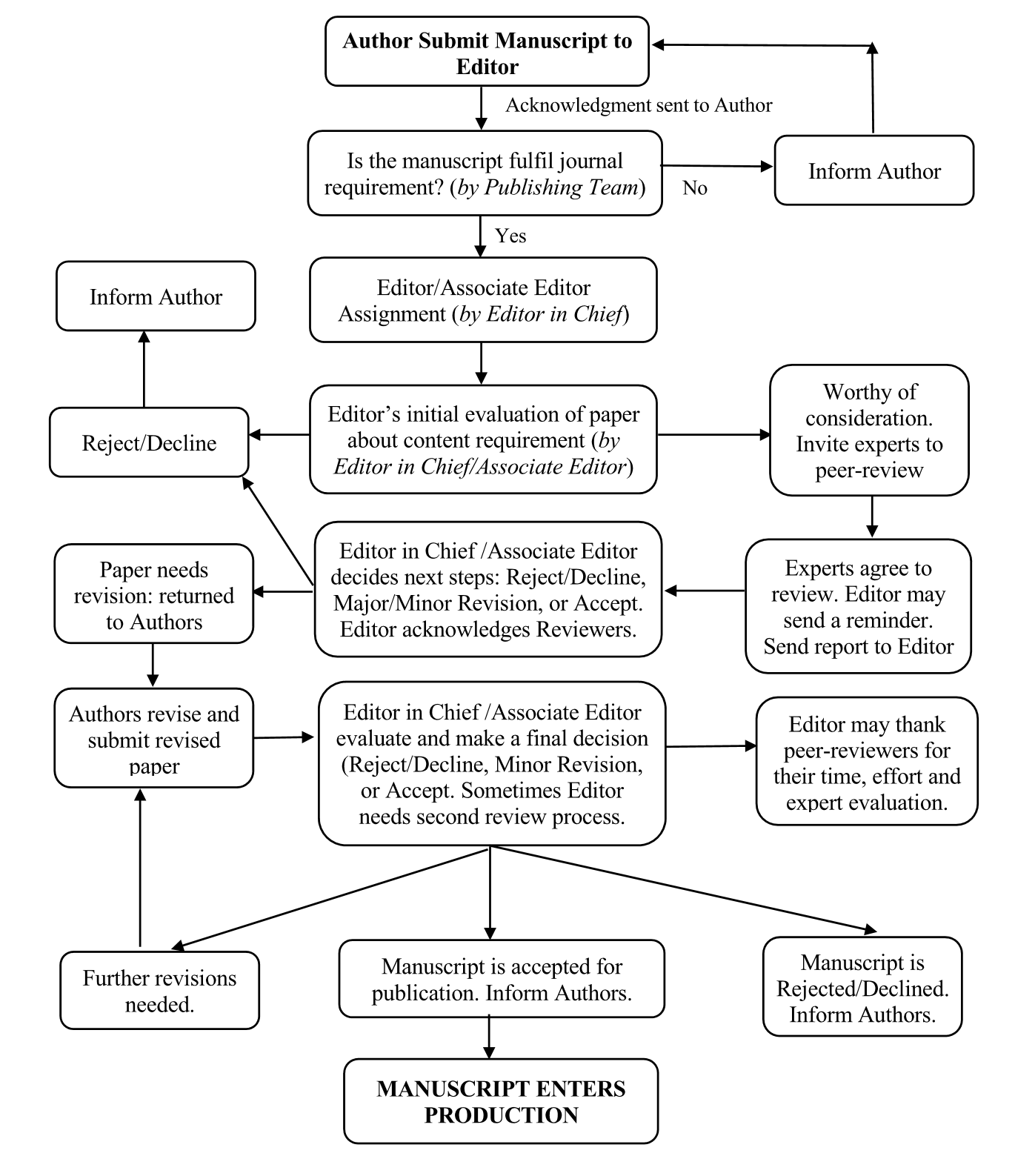
Criteria for Publication
In order to be approved for publication in International Journal of Cyber Forensics and Advanced Threat Investigations (CFATI), the following criteria should be regarded as a standard:
Completeness
A manuscript should be concisely and neatly written, nevertheless, completeness in argumentation, style, statistics, practical appliances, and used sources is the main factor of assessment for publication. If two different authors submit two articles with similar topics and conclusions, the one with more thorough and detailed text will be selected to be published.
Originality
Articles have to be originally written by their author(s), and any sources or other articles used in the work should be properly and clearly disclosed. The editorial board decides whether an article would be published or not, mostly by its novelty, significance of the subject matter, and practical appliance in the scientific discourse. All the submitted manuscripts will be thoroughly checked for plagiarism and novelty. All manuscripts submitted for publication to CFATI may be cross-checked for plagiarism using specific software. Similarity index should not exceed 20%
References
All the information used from other already published articles or scientific works should be clearly stated and cited following good academic conventions. References have to be fully and precisely acknowledged and put into the submitted manuscript as well as all the statistics and figures included in the article.
Metadata
All additional data, statistics, and other sources, which are used for the base of the article’s premises, have to be sent and published alongside the manuscript. It has to be accurately described with enough metadata and links to the used materials and articles in order to be easily reachable and discoverable.
Ethical aspects
All the articles submitted for publication should follow and cover the ethical conventions and not abuse the moral rights of other authors, communities, companies, organizations, institutions, etc.
Academic style and language standards
Articles must be neatly and concisely written, they have to be logically coherent and follow the academic style and formatting. All the arguments, premises, conclusions, and results should be clearly stated, and supported by the necessary referential data and sources. All the manuscripts should be written in grammatically correct English language. The authors will be asked to certify the level and quality of their text’s English language. Manuscripts written in poor English could be a subject of rejection prior to peer review.
Reasons For The Rejection of a Manuscript
The following reasons are adequate, alone or in combination, for rejection of a manuscript for publication:- The scientific content does not correspond to the journal’s aims and scope;
- The data are inadequate to support proper explanations or conclusions;
- Related work has been previously published and only a few new points have been added;
- The article contains accumulated information that has been previously published, with only a few technical improvements;
- The article is expected to attract only a very small portion of the journal’s readership audience;
- The article has been rejected previously and resubmitted without adding any new valuable content.
Publication Frequency
The International Journal of Cyber Forensics and Advanced Threat Investigations is published thrice a year in the spring, summer and fall. The submission will be open the whole year.
Open Access Policy
The International Journal of Cyber Forensics and Advanced Threat Investigations (CFATI) is a Gold-Open Access journal, which provides open access to its contents, believing that making research freely available to the public improves the global exchange of knowledge. CFATI adheres to the best practice and high publishing standards and complies with the following conditions:
• Provides immediate open access to its content on the principle that making research freely accessible online to the entire global research community, which ensures high visibility, maximizes exposure of published articles, and supports a greater global exchange of knowledge. Benefits of open access for authors include:
- Free access for all users worldwide
- High citations
- Increased visibility and readership
- Rapid publication
- Quality, reputable and high standard of peer-review
- Included in major bibliographic databases
- No spatial constraints
• CFATI also operates under the Creative Commons Licence CC-BY-SA. Authors are required to assign the copyright in their articles to Concept Tech Publishing. The intended copyright allows the distribution of the published material under a Creative Commons Attribution-ShareAlike 4.0 International License. Anyone may download, reuse, copy, reprint, distribute, or modify articles published in the journal, as long as they cite the original authors and source properly and any distribution of derivative works is under the same license as the original.
• Under the CC-BY-SA license, authors retain the copyright on their contributions but grant anyone the ability to download, reuse, reprint, modify, distribute, and/or copy materials published by CFATI, provided that the author and title of the journal are correctly cited. Authors are allowed to use their articles for any legal purposes deemed necessary without requesting permission from the journal with an acknowledgment of initial publication to this journal. This complies with the Budapest Open Access Initiative's definition of Open Access.
• CFATI deposits content with a long-term digital preservation or archiving program.
• CFATI uses DOIs as permanent identifiers.
• CFATI embeds machine-readable CC licensing information in articles.
• CFATI can provide article-level metadata for any indexers and aggregators
• CFATI has a deposit policy registered with a deposit policy registry, e.g. Sherpa/Romeo.
• CFATI is fully compliant with the requirements of Plan S, a key funder initiative to promote Open Access.
Archiving
The CFATI journal utilizes the PKP private LOCKSS network to create a distributed archiving system among participating libraries and permits those libraries to create permanent archives of the journal for purposes of preservation and restoration. More...

In Addition to that, all published articles are ingested by the Internet Archive Scholar service where the full-text is available. This is a long-term preservation facility.
Abstracting and Indexing Services
International Journal of Cyber Forensics and Advanced Threat Investigations is indexed with CrossRef and assigned a Digital Object Identifier (DOI). This means that all of our references are made available so that citations analysis can be tracked by the publishing community and Dimensions
International Journal of Cyber Forensics and Advanced Threat Investigations also implements Cited-by provided by Crossref. It intends to (1) easily navigate to related research, (2) see how the work has been received by the wider community, and; (3) explore how ideas evolve over time by highlighting connections between works.
We use a reference linking system to deposit all references for each article, so that, this feature can function properly (see our participation report).


We are always working to improve the quality of service for this journal, and to show that we have joined The Initiative for Open Citations I4OC and The Initiative for Open Abstracts I4OA to facilitate collaboration between scholarly publishers, infrastructure organizations, librarians, researchers and other interested parties to promote unrestricted availability of scholarly citation data and abstracts of the world's scholarly publications.
We work with our authors to help make their work as easy to discover as possible. International Journal of Cyber Forensics and Advanced Threat Investigations (CFATI) is currently included in the following abstracting and discovery services:












Additionally, The International Journal of Cyber Forensics and Advanced Threat Investigations (CFATI) is currently included in the discovery services of the following libraries :


































All of our article metadata is openly available for harvesting by indexing services via OAI-PMH and this journal is registered with Open Archives. We are also currently registered with the OAI Registry at University of Illinois at Urbana Champaign.
. Indexing in other international databases is under evaluation.
Language Accuracy and Plagiarism Policy
The Journal of Cyber Forensics and Advanced Threat Investigations emphasizes on language accuracy. It must be written in English with clear and concise grammatical English. The authors are suggested to have the manuscript checked by a colleague or reputable institution.
CFATI journal also concerns about the originality of the article. Plagiarism is intolerable. The article will be banished, and the author will be rejected for future submission.
For screening language accuracy and plagiarism check, CFATI uses several tools including:
• Grammarly
• LanguageTool
• Ludwig
• Duplicate Checker
• Quetext
Plagiarism Policy
The International Journal of Cyber Forensics and Advanced Threat Investigations (CFATI) Editorial Board recognizes that plagiarism is not acceptable and therefore establishes the following policy stating specific actions (penalties) when plagiarism is identified in an article that is submitted for publication in CFATI.
Definition:
Plagiarism involves the "use or close imitation of the language and thoughts of another author and the representation of them as one's own original work."
Policy:
Articles must be original, unpublished, and not pending publication elsewhere. Any material taken verbatim from another source needs to be clearly identified as different from the present original text by (1) indentation, (2) use of quotation marks, and (3) identification of the source.
Any text of an amount exceeding fair use standards (herein defined as more than two or three sentences or the equivalent thereof) or any graphic material reproduced from another source requires permission from the copyright holder and, if feasible, the original author(s) and also requires identification of the source; e.g., previous publication.
All submitted articles will be checked for their similarity via plagiarism software.
When plagiarism is identified, the Editor-in-Chief responsible for the review of this article and will agree on measures according to the extent of plagiarism detected in the article in agreement with the following guidelines:
Level of Plagiarism
1.Minor: A short section of another article is plagiarized without any significant data or idea taken from the other article
----Action: A warning is given to the authors and a request to change the text and properly cite the original article is made
2.Intermediate: A significant portion of a article is plagiarized without proper citation to the original article
----Action: The submitted article is rejected and the authors are forbidden to submit further articles for one year.
3. Severe: A significant portion of a article is plagiarized that involves reproducing original results or ideas presented in another publication
----Action: The article is rejected and the authors are forbidden to submit further articles to our journals and conferences for five years and their home institutions will be notified about this unethical behavior.
It is understood that all authors are responsible for the content of their submitted article as they all sign the CFATI Copyright Transfer Form. If a penalty is imposed for plagiarism, all authors will be subject to the same penalty.
If a second case of plagiarism by the same author(s) is identified, a decision on the measures to be enforced will be made by the Editorial board (Editor-in-Chief, and Editorial members) with the Chair of the Editor-in-Chief. The author(s) might be forbidden to submit further articles forever and their home institutions will be notified about this unethical behavior. We will add these authors to the CFATI blacklist and share it with our colleagues and program committee members who interact with us. Furthermore, we are planning to add some intentional authors in the CFATI blacklist to the IEEE prohibited authors list. As known, the authors, who are listed in the IEEE prohibited authors list, will be prohibited from submitting to all IEEE publications for 2-3 years.
This policy applies also to material reproduced from another publication by the same author(s). If an author uses text or figures that have previously been published, the corresponding paragraphs or figures should be identified and the previous publication referenced. It is understood that in the case of a review article or article of a tutorial nature much of the material was previously published.
The author should identify the source of the previously published material and obtain permission from the original author and the publisher. If an author submits a manuscript to CFATI with significant overlap with a manuscript submitted to another journal simultaneously, and this overlap is discovered during the review process or after the publications of both articles, the editor of the other journal is notified and the case is treated as a severe plagiarism case. Significant overlap means the use of identical or almost identical figures and identical or slightly modified text for one-half or more of the article. For self-plagiarism of less than one-half of the article but more than one-tenth of the article, the case shall be treated as intermediate plagiarism. If self-plagiarism is confined to the methods section, the case shall be considered as minor plagiarism.
If an author uses some of his/her previously published material to clarify the presentation of new results, the previously published material shall be identified and the difference to the present publication shall be mentioned. Permission to republish must be obtained from the copyright holder. In the case of a manuscript that was originally published in conference proceedings and then is submitted for publication in CFATI either in identical or in expanded form, the authors must identify the name of the conference proceedings and the date of the publication and obtain permission to republish from the copyright holder. The editor may decide not to accept this article for publication.
However, an author shall be permitted to use material from an unpublished presentation, including visual displays, in a subsequent journal publication. In the case of a publication being submitted, that was originally published in another language, the title, date, and journal of the original publication must be identified by the authors, and the copyright must be obtained. The editor may accept such a translated publication to bring it to the attention of a wider audience. The editor may select a specific article that had been published (e.g. a “historic” article) for republication in order to provide a better perspective of a series of articles published in one issue of CFATI. This republication shall be clearly identified as such and the date and journal of the original publication shall be given, and the permission of the author(s) and the publisher shall be obtained.
The CFATI layout editor for the Journal is responsible for maintaining the list of authors subjected to penalties and will check that no authors of a submitted article are on this list. If a banned author is identified, the layout editor will inform the Editor-in-Chief who will take appropriate measures. This policy will be posted on the website with the instructions for submitting a manuscript, and a copy will be sent to the authors with the confirmation email upon initial receipt of their original manuscript. A sentence shall be added to the copyright transfer form to indicate that the author(s) have read the Plagiarism Policy.
Publication Ethics and Malpractice Statement
Concept Tech Publishing is an independent private organization that publishes peer-reviewed scholarly journals covering a wide range of academic disciplines and is devoted to promoting researches and technologies in related fields of cybersecurity, digital forensics, incident response, and threat investigations, through digital technology. Concept Tech Publishing Journals are peer-reviewed international journals. This statement clarifies the ethical behavior of all parties involved in the act of publishing an article in our journals, including the authors, the editors, the peer-reviewers, and the publisher (Concept Tech Publishing). This statement is based on COPE’s Best Practice Guidelines for Journal Editors. Continue Reading ....
Competing Interest Guidelines
Public trust in the peer-review process and the credibility of published articles depend in part on how well-competing interests are handled during writing, peer review, and editorial decision making.
Competing interests exist when an author (or the author’s institution), reviewer, or editor has financial or personal relationships that inappropriately influence (bias) his or her actions. These relationships vary from those with negligible potential to those with great potential to influence judgment, and not all relationships represent true competing interests. The potential for competing interests can exist whether or not an individual believes that the relationship affects his or her scientific judgment.
Financial relationships (such as employment, consultancies, stock ownership, honoraria, paid expert testimony) are the most easily identifiable competing interests and the most likely to undermine the credibility of the journal, the authors, and of science itself. However, conflicts can occur for other reasons, such as personal relationships, academic competition, and intellectual passion.
All participants in the peer review and publication process must disclose all relationships that could be viewed as presenting a potential competing interest.
Editors may use information disclosed in competing interest statements as a basis for editorial decisions. Editors will publish this information if they believe it is important in judging the manuscript.
Earlier Publications on the Same Research
The journal does not mind if the research that is being submitted for consideration of publication has already been previously published in bits and pieces at workshops and conferences (but not journals), as long as the compilation of earlier research reports plus new materials provides significant new insights and added value. Authors should clearly explain the relationship of their submission to their prior publications, and point out the significant added value of their submission in comparison to their prior publications. The Publisher also accepts manuscripts that have prior versions on non-commercial pre-print sites such as arXiv.org and blogs.
Any media coverage that prior publication may garner, will not change or hinder the editorial process. If this arises, the author(s) may wish to provide clarity of the stage and timing of the work in relation to it being published and peer-reviewed.
Errata and Corrigenda
Changes/additions to accepted articles
All content of published articles is subject to the editorial review process, organized by and under the auspices of the editor. Should the authors wish to add to their article after acceptance, they must submit a request to the editor and the new content will be reviewed.
• If the new material is added to the accepted article, it must be submitted for peer review as a new manuscript, referring back to the original;
• If the new material should replace the original content of the accepted article, the editor may consider the publication of an erratum or a corrigendum.
Erratum
An erratum refers to a correction of errors introduced to the article by the publisher.
All publisher-introduced changes are highlighted to the author at the proof stage and any errors are ideally identified by the author and corrected by the publisher before final publication.
Corrigendum
A corrigendum refers to a change to their article that the author wishes to publish at any time after acceptance. Authors should contact the editor of the journal who will determine the impact of the change and decide on the appropriate course of action.
Deposit and Self-Archiving
Preprint/Postprint /Publisher's version use of CFATI Journal Content-Sherpa/Romeo
Preprint Use of CFATI Content
A preprint is defined here as the un-refereed author version of an article. Authors can archive preprint version of the article on their own personal website and/or that of their employer and/or in free public servers of preprints and/or articles in their subject area.
Postprint Use of CFATI Content
A postprint is defined here as the final draft author manuscript, as accepted for publication by the journal, including modifications based on reviewers’ suggestions before it has undergone copyediting and proof correction. Authors can archive their accepted postprint manuscript PDF to an institutional and/or centrally organized repository.
Publisher's version Use of CFATI Content
A publisher version/PDF is defined here as the final official version of the manuscript, After having been professionally typeset, copyedited, and formatted accordingly by Concept Tech Publishing, as published on the journal's website, Authors can and encouraged to deposit the final published article PDF in their institutional repository or any suitable subject repository, to share and promote their research to a broader audience, to get more citations, and to cultivate a strong reputation. When uploading the published manuscript to a repository, authors should include a credit line (see below) and a link to the final published version of the article. This will guarantee that the definitive version is readily available to those accessing the article from public repositories, and means that the article is more likely to be cited correctly:
"This is a copyedited, publisher-produced PDF of an article published in the International Journal of Cyber Forensics and Advanced Threat Investigations (CFATI): [year], [DOI Number]. Some rights reserved. The definitive publisher-authenticated version [insert complete citation information here] is available online at [insert URL of the published article on the journal's website, received upon publication here]."
Retraction
An article published in the International Journal of Cyber Forensics and Advanced Threat Investigations will be considered for retraction in the publication if:
- There has been clear evidence that the findings are unreliable, either as a result of misconduct (e.g. data fabrication) or honest error (e.g. miscalculation or experimental error).
- The findings have previously been published elsewhere without proper cross-referencing, permission, or justification (i.e. cases of redundant publication).
- The article constitutes plagiarism.
- The article reports unethical research.
The mechanism of retraction follows the Retraction Guidelines of the Committee on Publication Ethics (COPE).
Withdrawal of Manuscripts
The International Journal of Cyber Forensics and Advanced Threat Investigations (CFATI) is an open-access journal, free to access, read and print. There are no charges for submitting manuscripts or publishing accepted articles. There is no pay-per-view, pay-per-print fee for the published accepted articles. There are no editorial/peer-review charges being solicited from the authors. However, this model should not be exploited. Authors are not allowed to withdraw submitted manuscripts, because the withdrawals are a waste of valuable resources; the editors and referees spent a great deal of time processing submitted manuscripts, money, and technical works that are invested by the publisher.
If authors still request withdrawal of their manuscripts when the manuscripts are still in the peer-reviewing process, authors will be punished with paying GBP 1250 per manuscript, as a withdrawal penalty to the publisher. However, it is unethical to withdraw a submitted manuscript from one journal if accepted by another journal. The withdrawal of manuscripts after the manuscripts are accepted for publication, the author will be punished by paying GBP 2250 per manuscript. Withdrawal of manuscripts is only allowed after the withdrawal penalty has been fully paid to the Publisher. If the author doesn't agree to pay the penalty, the authors and their affiliations will be blacklisted for publication in this journal and their home institutions will be notified about this unethical behavior. Even, their previously published articles will be removed from our online system. A retraction notice will be published online replacing the original withdrawn manuscript. If the article already appeared in a print issue, a retraction notice will be published in the next available issue, which refers to the already published article.
Research Ethics Policy
Concept Tech Publishing expects all prospective authors to read and understand our Research Ethics Policy before submitting any manuscripts to the International Journal of Cyber Forensics and Advanced Threat Investigations (CFATI). The publication of an article in a peer-reviewed journal is a direct reflection of the quality of work of the author and the institutions that support them. Peer-reviewed articles use the scientific method and must comply with standards of expected ethical behavior.
Please note that all submitted manuscripts are subject to checks using anti-plagiarism software to detect overlapping and similar text. The anti-plagiarism software checks submissions against tens of millions of published research papers, documents on the web, and other relevant sources. There are no numerical limits assigned to these behaviors, and the Editors will personally ask for clarifications if needed. If plagiarism or misconduct is suspected, the editors may ask for clarification. If the additional information is insufficient, the manuscript may be rejected. Continue Reading ....
Complaints
We aim to respond to and resolve all complaints quickly and constructively. The procedures to investigate and resolve complaints followed by the Journal of Cyber Forensics and Advanced Threat Investigations aims to be fair and balanced for those making complaints and for those being complained about. The complaint can be made by writing an email.
All complaints will be acknowledged within three working days.
Please email to: cfati@conceptechint.net







